![]()
Employee Satisfaction Surveys | Phishing Campaigns
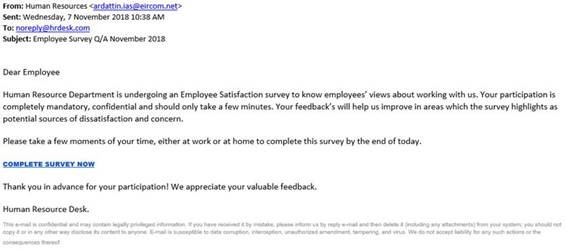
Phishing campaigns involving employee satisfaction surveys have been found to be doing the rounds again. As you can see in the following screenshot, the phishing email uses emotive language like “your participation is completely mandatory” to attempt to coerce the recipient into clicking on the link.
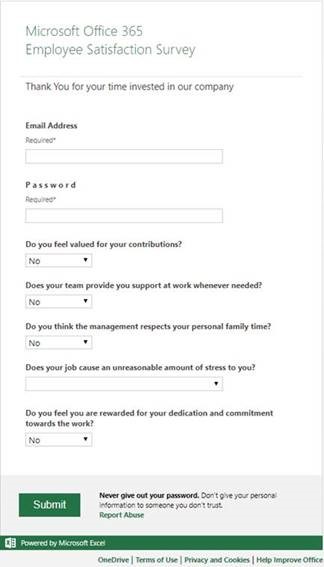
If the recipient clicks through (please don’t!) they are presented with the following form, which asks them to enter their username and password and answer a number of questions. Ironically, the form reminds the user that they should “Never give out your password” and “Don’t give your personal information to someone you don’t trust."
As a general recommendation, if you receive such emails, please check with the appropriate department (in this case, HR) to determine the validity of the request. Departments who are responsible for running such surveys are also recommended to inform users in advance of any survey campaigns and instruct users to only engage in surveys if they have received prior notification of a campaign.
Cisco Stealthwatch, ASA and Firepower Vulnerabilities
Back in November, we saw Cisco have released a security advisory for a critical vulnerability in the Stealthwatch Management Console of Stealthwatch Enterprise which could allow an unauthenticated, remote attacker to bypass authentication and execute arbitrary actions with administrative privileges on the affected system. The vulnerability affects Cisco Stealthwatch Enterprise 6.10.2 and earlier. Cisco has released updates for minor release trains 6.7, 6.8, 6.9, and 6.10 to address this vulnerability. Cisco Stealthwatch Enterprise customers are recommended to review the advisory and upgrade their systems accordingly.
Multiple newswires, including IT News, reported that Cisco ASA and Firepower firewalls are vulnerable to a SIP-based Denial of Service (DoS) attack that can crash the devices. The vulnerability is in the inspection engine of Cisco’s ASA Software Release 9.4, FTD Software Release 6.0 and later. Customers who are running affected devices can mitigate the vulnerability by either disabling SIP inspection or blocking the invalid 'Sent-By' address of 0.0.0.0. Further information on affected devices and recommendations can be found in the Cisco security advisory for this vulnerability.
US Cyber Command starts contributing Malware samples to VirusTotal
ZDNet is reporting that the Cyber National Mission Force (CNMF), part of the US Cyber Command (USCYBERCOM), has started sharing malware samples discovered on the DOD’s networks with VirusTotal – an online file scanning service and Malware repository that was purchased by Google in 2012.
The CSO of Chronicle, Alphabet’s cyber-security division (Alphabet is Google’s parent company), said that “the first submission, for LoJack Malware, included files that weren't previously in VirusTotal”. Kaspersky has been tracking the LoJack malware since September 2014, which has been attributed to APT28 (associated with the Russian GRU).
This report reinforces the need for and the power of shared threat intelligence, which underpins the concept of herd immunity or 'see once, block everywhere'. In order for herd immunity to work, more organisations must contribute, and the barriers to sharing of threat intelligence have to be torn down – this is the idea behind the Cyber Threat Alliance, of which many of our vendor partners are members.
Contact Us today to find out how Thomas Duryea Logicalis can support you with your organisation's security concerns and posture.



